What is a VPN

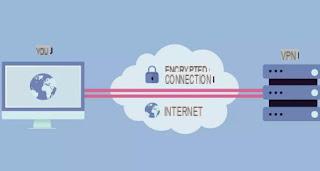
Before we get into the heart of this tutorial, I want to explain the exact meaning of the term VPN to you. VPN is the acronym of the English phrase Virtual Private Network, ie "virtual private network" and describes a technique that, thanks to a particular system called tunneling, allows both to make your activities on the Net invisible to unauthorized eyes (for example cybercriminals or government censorship bodies) and to mask the IP address from which you access the Internet.
This result is obtained by creating, among the computers involved, a real one private network, accessible only to authorized users. That network is virtual, that is, created by exploiting the means of communication Internet and not a set of cables or other physical systems (which, however, happens with classic home networks). As I have already mentioned above, there are different scenarios that involve the use of a VPN, therefore this type of network can be "built" in a different way depending on the case in which it is necessary to use it. To be clear, you can distinguish VPNs into two broad categories of use.
- VPN hub-and-spokes, which are used to connect the various nodes of the network (computer, smartphone, tablet, etc.) to a "central office" (the VPN server). The "central office" takes care of protecting the traffic and sorting it between the connected nodes. Usually this type of VPN is used for IP camouflage and data protection activities over unsecured connections.
- VPN site-to-site which, on the other hand, is typically used in the connection of two or more different private networks (both in terms of structure and position) through a secure connection, using an insecure channel (Internet). This approach is often used in a business environment, to allow the secure exchange of data and information between two or more locations of the same company.
Also with regard to security, VPNs can be structured with different characteristics. For example, in those that define themselves Trusted VPN, and the service manager to decide and optimize the data path (thus paying attention to the quality of communication), dealing with the available means to prevent access to unauthorized users. This ensures that the data arrives quickly at its destination, but does not offer absolute security about the protection of it.
Due to this lack of security, as the Internet spreads, it has become necessary to apply additional measures. The Secure VPN, virtual private networks that guarantee data protection by creating a tunnel between the two nodes of the network. This mechanism, however, cannot guarantee that the data path is optimal: it is for this reason that, to date, the most used type of VPN is a "mix" between the two mentioned above. This mix is defined Hybrid VPN and allows you to have VPNs that combine the speed of communication offered by Trusted VPNs with the security guaranteed by the tunneling technology used in Secure VPNs.
What does tunneling mean
So far I have explained to you what VPNs are and how they are divided, mentioning the tunnel communication that is created between one node and another. Before entering into the merits of the matter, however, it is good that you know the fundamentals of the passage of data through the Internet.
When a device connected to the large network sends information, it comes encapsulated, that is, "closed" in gods packages; the latter contain, in addition to the data itself, also other information, such as the IP address of the sender, the IP address of the recipient, the type of data, the network path, etc., which are defined in jargon header. Despite some data traveling in a way encrypted (for example in connections HTTPS), the packet header is visible to anyone with access to the communication channel, which in this case is the Internet and is common.
It is precisely in the light of this reason that, in order to guarantee a secure VPN connection in which the information in transit (including headers) is available only to the two nodes involved in the communication, the need arises to create a private channel that puts them in communication: this operation is called tunneling. The created channel is called tunnel and allows the transit of information in a completely "invisible" way, while using a public means of communication such as the Internet.

To clarify your ideas, think of the Internet as a road network in which many cars (information) pass, then imagine an observer on a helicopter who scrutinizes everything: he would be able to see what happens between the cars entering a gallery (the tunnel)? Obviously not: he would be able to examine what goes into the latter and what comes out but, if the motorists decide to exchange cars inside the tunnel, the outside observer would not notice.
Encryption protocols

Now that you fully understand the concept of a tunnel, it's good to understand how VPNs guarantee data invulnerability: the secret is to apply a protocol of encryption, that is, a method of disguising the original data, transforming it into other data that can only be understood by the intended recipient.
As for VPNs, there are many existing encryption protocols, each with its strengths and weaknesses: below I describe the most important ones.
- PPTP - is a protocol developed by Microsoft, certainly one of the most popular and used to protect VPN connections. Despite being fully integrated across all software platforms, PPTP contains numerous vulnerabilities and, since 2012, is considered obsolete and advised against by Microsoft itself. I recommend that you rely on VPN services that use PPTP only to hide your real IP address, not for any other purpose.
- SSTP - successor of PPTP, it is a protocol designed by Microsoft and today considered safe. It is mainly used on Windows-based VPNs.
- IPsec - it is a protocol that deals with the encryption of data on the Internet. IPsec is widespread and implemented in most operating systems and is considered secure. As for VPN connections, IPsec works in conjunction with the protocol L2TP (whose task is to create the actual tunnel).
- IKEv2 - born from the collaboration between Cisco and Microsoft, it is a protocol quite similar to IPsec but considered much more secure, and integrated in many VPN client (i.e. programs that allow access to this service). Among the strengths of IKEv2 are performance (data travels fast) and extreme flexibility of use, which makes it a favorite when it comes to using VPNs via mobile.
- OpenVPN - it is one of the most used solutions in the field of VPNs today: it supports many encryption algorithms, it is by nature . and adapts to numerous application scenarios. Configuring OpenVPN can be quite complex for the user: for this reason, the various VPN services allow you to download pre-made programs, based on OpenVPN, but pre-configured and ready to be easily installed.
In very simple terms, for "important" operations I would like to recommend the protocols IKEv2 e OpenVPN, as they guarantee security in data exchange and, at the same time, communication speed.
How to choose a VPN

I am sure that, at this point, you have made the concept of VPN your own and have perfectly understood all its features. Now is the time to put your learning into practice and choose the type of VPN that's right for you.
If you own a company and are thinking of implementing a VPN system to allow your employees to work from home, the advice I can give you is to contact an expert consultant on the subject and let me show you the most suitable solution. your apparatus. If, on the other hand, you are looking for a VPN service that can protect your connection or mask your IP address, you need to consider a number of factors that I am going to illustrate below.
- Cost - there are free and paid VPN services. The former, in most cases, impose limits on the amount of monthly traffic. When it comes to paid VPNs, make sure that the quality of the service offered is appropriate for the proposed price.
- Information gathering - some VPNs, especially the free ones, collect anonymous information on the operations carried out by the user for advertising and / or profiling purposes. Although it may be apparently harmless, I advise you to avoid using these services if you intend to operate with delicate, sensitive or worse still subject to censorship / persecution data. Read carefully the terms of use of the VPN service you choose to make sure it does not collect information about your activities.
- Number of servers - usually, a VPN with few servers does not guarantee a great communication speed. Generally speaking, the more servers the VPN offers, the higher the connection performance.
- Location of servers - numerous VPN services offer servers located in many parts of the world, this to ensure that the IP address displayed from the outside can be changed if necessary. If you are looking for a service that can bypass regional blocks, pay close attention to this aspect.
- Encryption protocol - there is nothing more to add, I told you extensively in the previous section.
Best VPNs
How do you say? While everything is clear, you don't know where to start to choose a VPN that suits your needs? Don't worry, I think I have what you need.
NordVPN

NordVPN is one of the most famous and popular VPN services available on the market. It is compatible with all popular devices and operating systems: Windows, MacOS, Linux, Android, iOS / iPadOS, Smart TV Android TV, Raspberry Pi, NAS, router etc. and can count on many servers, all very reliable, scattered all over the globe.
This allows for super-secure browsing, characterized by very advanced encryption, even on public Wi-Fi networks (not even NordVPN operators can trace the browsing data, as nothing is recorded of the activities carried out by users); to overcome all regional restrictions and to access foreign catalogs of streaming services. Additionally, there are servers specifically dedicated to P2P, to online browsing via protocol Onion (the one used by the anonymous network Tor) and browsing with dedicated IP.
To use NordVPN, you need to connect to the service's official website, choose a plan from those available and create an account. The available plans are as follows: 2 or 3 anni in base alle promo in corso less than 3 euros / month (billed annually); 2 years at 2,97 euros / month (billed annually), 1 year at 3,93 euros / month (billed annually) or 1 month to 9,56 euros. All with a 30-day money back guarantee and with the possibility of using the service on up to 6 devices at the same time. Furthermore, during the promo periods, the price also includes extras (eg the password manager North Pass, worth $ 194.61).
Once you have created your account and chosen the plan to use, you need to download the NordVPN client and install it on your devices. For example, if you use a PC equipped with Windows, you have to open the .exe file obtained, click on the button Yes, wait for all the files necessary for the correct functioning of the program to be downloaded from the Internet and press the buttons Next, install e Finish, to conclude the setup. If you use a Macinstead, you need to download NordVPN from the Mac App Store.
On smartphones and tablets, everything is even simpler: open the store of your device (eg Play Store on Android or App Store on iPhone / iPad), search NordVPN in the latter and first tap onicona dell'applicazione (in the search results) and then on the button Installa / Ottieni. On iOS / iPadOS you may be prompted to verify your identity via Face ID, Touch ID, or Apple ID password.
When installation is complete, start the client NordVPN, make the Log In to your account and select the VPN server to connect to - you can choose a server based on its nationality, based on its type (in section Specialty servers find servers optimized for P2P, browsing via protocol Onion o Dedicated IP) or you can make one search, to find the server you prefer.
Once the connection is established, open the browser and / or the programs you want to use to take advantage of your secure connection and that's it. Afterward, to disconnect from the VPN, open NordVPN and click on the button Disconnect. For more details, I invite you to read my NordVPN review.
Surfshark

Surfshark it is an advanced but at the same time very simple to use VPN solution. It allows you to bypass regional restrictions, censorships and access foreign catalogs of streaming services via more than 1040 server scattered over 61 Countries around the world.
The service is available on computers (Windows, macOS and Linux, also via extension for Chrome and Firefox browsers), on smartphones and tablets (Android and iOS / iPadOS), on Amazon Fire TV Stick), Smart TV, Apple TV, PlayStation , Xbox, and other devices that don't support VPN installation, using Surfshark's intelligent DNS service. It is allowed to be used on multiple devices at the same time and, thanks to the AES 256-bit encryption, all communications are impossible to intercept by potential attackers, Internet providers and by the Surfshark managers themselves (which do not register anything ).
To the list of features offered by Surfshark must also be added Whitelister, which allows you to create a list of exceptions with programs that should not use the VPN; CleanWeb, which allows you to protect yourself from malware and other harmful or annoying content online, e Kill Switch, which allows you to automatically disable the Internet connection in case of disconnection from the VPN.
There are several plans to use Surfshark: the one from 24 months for € 1,79 / month (billed every 24 months); the one from 12 months for € 4,99 / month (with annual billing) and that from 1 month for 9,89 euros. There is always a 30 day money back guarantee.
To activate your Surfshark account and start using the service on your PC, then connect to the official Surfshark website, click on the button Buy it now and choose the plan you want to subscribe. Many payment methods are supported: credit card, PayPal, Google Pay, I suffer, Amazon Pay o Cryptocurrency.
Once the account has been created, download the Surfshark client that best suits the operating system installed on your PC, such as Windows or macOS, by connecting to the official website of the service. After that, to install the software on Windows, launch the .exe file you have obtained and click on the button Yes; to install it on MacOSinstead, you can use the Mac App Store or package .dmg taken from the Surfshark site.
On smartphones and tablets, you can install Surfshark by opening the relevant section of the Android and iOS / iPadOS stores and pressing the button Installa / Ottieni. On iOS / iPadOS, you may also need to verify your identity via Face ID, Touch ID, or Apple ID password.
Once the installation is complete, start Surfshark on your device, choose if create an account o enter to an existing account and press the button Connect, to automatically connect to the fastest VPN server. Alternatively, go to the section Positions and choose the server you want to connect to.
At the end of the safe browsing session, press the button Disconnect, so you can disconnect from the VPN, and that's it. More information is available on the official Surfshark website.
Article made in collaboration with NordVPN and Surfshark.
VPN: how it works